Cybersecurity Trends to Secure Your Future in 2024-2025
As we head into 2024 and then some, network safety stays a main concern. The scene is steadily changing, and remaining on the ball is critical for the two people and organizations. How about we jump into the key network safety drifts that you really want to watch in the impending years.
- The Force of computer based intelligence and AI
- Embracing Zero Trust Design
- Combating the Ransomware Threat Ransomware remains a significant threat
- Getting the Web of Things (IoT)
- Exploring Administrative Consistency
- Protecting the Cloud
- Helping Representative Preparation
- Exploring Quantum Cryptography
- Conclusion
- FAQS
The Force of computer based intelligence and AI
Computer-based intelligence and AI are major advantages in online protection. These advancements can rapidly dissect gigantic measures of information, assisting with distinguishing and answer dangers continuously. They’re becoming irreplaceable for staying aware of the modern strategies of cybercriminals.

Embracing Zero Trust Design
The Zero Trust model is picking up speed. It works on the idea that threats can come from anywhere, both outside your network and inside it. This means that every user and device needs to be checked, which makes security better overall.
Combating the Ransomware Threat Ransomware remains a significant threat
Businesses, healthcare providers, and government agencies are all targets of cybercriminals. To counter this, it is more important than ever to have reliable backup plans and robust detection systems.
Getting the Web of Things (IoT)
Our reality is becoming more associated, on account of the Web of Things (IoT). While helpful, this additionally presents new weaknesses. Improving security for these gadgets through better confirmation and organization division is significant.
Exploring Administrative Consistency
Network safety guidelines are getting stricter around the world. To avoid penalties and safeguard confidential information, it is essential to keep up with these changes. Remaining consistent will be a critical concentration for some associations.
Protecting the Cloud
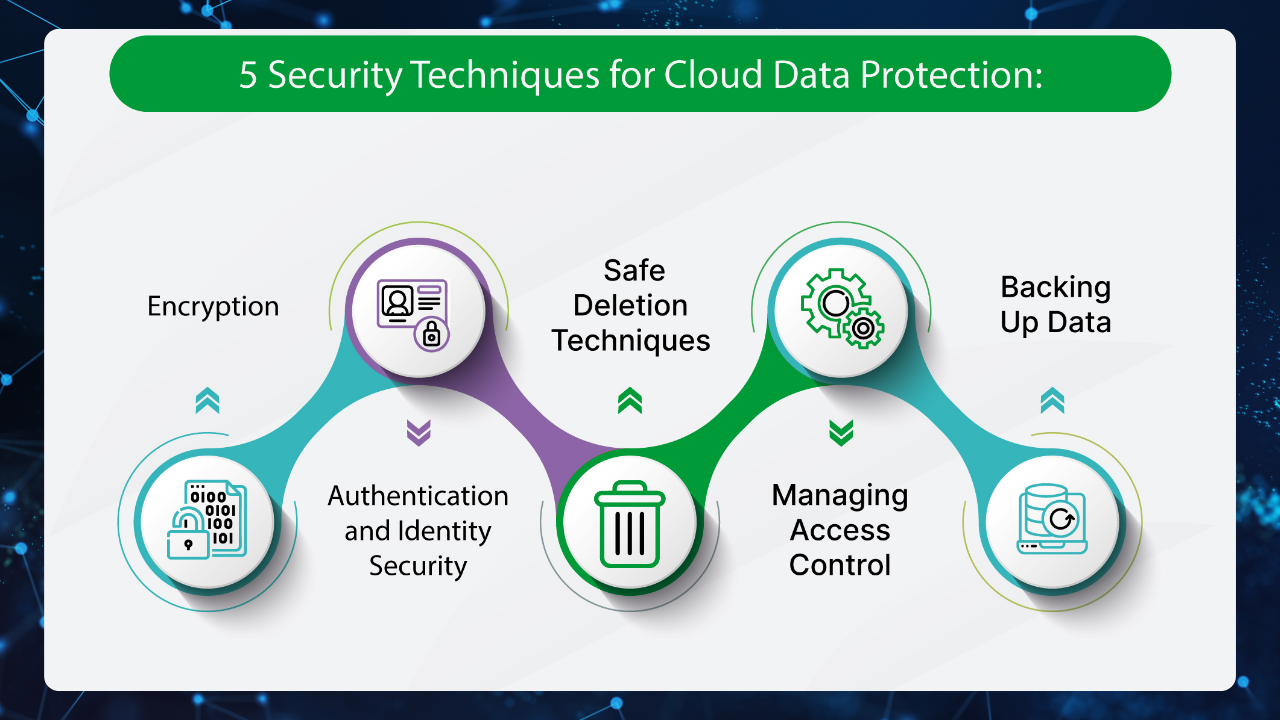
Keeping the Cloud Safe As more data moves to the cloud, it’s important to make sure these places are safe. This incorporates utilizing progressed encryption, getting access controls, and performing standard security checks to protect cloud-based resources.
Helping Representative Preparation
Human blunder is a critical network protection risk. Executing extensive preparation projects to instruct workers on phishing, secret word the board, and safe internet-based practices can enormously improve security.
Quantum Cryptography
An Investigation Quantum computing presents both challenges and opportunities. It can break conventional encryption techniques yet additionally presents quantum cryptography, offering phenomenal security. Staying aware of these progressions will be fundamental for future-sealing your safety efforts.
Network protection is a continually developing field. You can stay ahead of potential threats in 2024 and beyond by actively improving your security measures and keeping an eye on these trends. In this digital age, the best defense is to remain informed and prepared.
For more information and to enhance your online presence, visit DOnline360, a digital communication agency offering comprehensive services including web design and development, digital marketing, SEO, content creation, and social media management. DOnline360 focuses on creating visually appealing, functional, and user-friendly websites tailored to their clients’ needs.
FAQs
1. What is the Zero Trust Architecture?
Zero Trust Architecture is a security model that requires strict verification for every user and device accessing resources, assuming that threats can come from both inside and outside the network.
2. How does AI enhance cybersecurity?
AI can analyze vast amounts of data quickly, detecting and responding to threats in real-time, thus enhancing overall cybersecurity by identifying and mitigating sophisticated attacks.
3. Why is ransomware still a major threat?
Ransomware attacks are lucrative for cybercriminals, targeting various sectors from businesses to healthcare, causing significant disruption and financial loss. Robust detection and backup strategies are crucial for mitigation.
4. What are the key concerns with IoT security?
The rapid expansion of IoT introduces vulnerabilities due to the increased number of connected devices. Enhancing device authentication and network segmentation are essential for improving IoT security.
5. How are cybersecurity regulations changing?
Governments are implementing stricter regulations to protect sensitive data. Staying compliant with these evolving standards is essential to avoid penalties and ensure data security.
6. What are the best practices for cloud security?
To protect cloud environments, it’s important to use advanced encryption methods, secure access controls, and conduct regular security assessments.
7. Why is employee training important in cybersecurity?
Human error is a major cybersecurity risk. Comprehensive training programs educate employees on phishing scams, password management, and safe online practices, which helps in creating a secure organizational culture.
8. What is quantum cryptography?
Quantum cryptography leverages the principles of quantum mechanics to create highly secure encryption methods, potentially providing unprecedented security against future cyber threats.
9. How can I stay updated on cybersecurity trends?
Staying informed through industry news, following cybersecurity experts, and participating in relevant courses and webinars can help you stay updated on the latest trends and best practices.
10. What should I do if my organization is targeted by a cyber attack?
In case of a cyber attack, it’s important to have an incident response plan in place. This includes identifying the breach, containing the threat, assessing the damage, and communicating with stakeholders. Additionally, report the incident to the relevant authorities and review your security measures to prevent future attacks.








